Scanning Target Hosts with unicorn scan
Scanning a hosts most of the time multiple hosts for open ports and services discovery is one of first thing most of the penetration testers do , so in this post I am going to show you how to use unicorn scan and how to perform scan against single and multiple targets .
PLEASE NOTE : For demonstration purpose , I’ll be using kali Linux as my primary os and ubuntu and windows virtual machines as target hosts with running several service .
Features
- Asynchronous stateless TCP scanning with all variations of TCP Flags.
- Asynchronous stateless TCP banner grabbing
- Asynchronous protocol specific UDP Scanning (sending enough of a signature to elicit a response).
- Active and Passive remote OS, application, and component identification by analyzing responses.
- PCAP file logging and filtering
- Relational database output
- Custom module support
- Customized data-set views
Scanning
Lets see how to perform simple scan , Basic TCP SYN scan
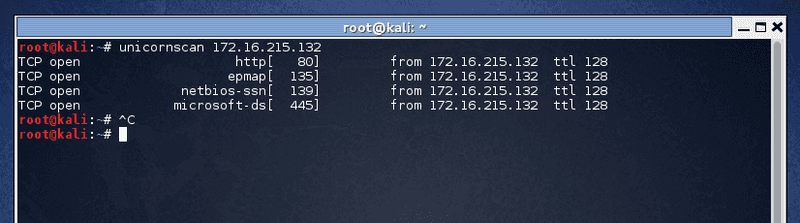
root@kali:~# unicornscan 172.16.215.132Sample Output :
root@kali:~# unicornscan 172.16.215.132
TCP open http[ 80] from 172.16.215.132 ttl 128
TCP open epmap[ 135] from 172.16.215.132 ttl 128
TCP open netbios-ssn[ 139] from 172.16.215.132 ttl 128
TCP open microsoft-ds[ 445] from 172.16.215.132 ttl 128 UDP Scan
root@kali:~# unicornscan -mU -r200 -I 192.168.100.1:53Where
__________________________________________________________________
-mU : is mode UDP
-I : Display Immediately
192.168.100.1 : target IP
:53 : port number
-r200 : 200 Packets per second
___________________________________________________________________Sample Output
UDP open 192.168.100.1:53 ttl 128
UDP open domain[ 53] from 192.168.100.1 ttl 128TCP Scan
root@kali:~# unicornscan -r500 -mT 192.168.100.1/24:80,443,445,339Where
__________________________________________________________________
-mT : is mode TCP
192.168.100.1/24 : target network range ( block )
:80,443,445 : ports
-r500 : 500 Packets per second
___________________________________________________________________Many Other options you can pass , for example for ACK use -mTsA
SYN : -mT
ACK scan : -mTsA
Fin scan : -mTsF
Null scan : -mTs
Xmas scan : -mTsFPU
Connect Scan : -msf -Iv
scan with all options : -mTFSRPAUEC
Syn + osdetect : -eosdetect -Iv (-mT)
scan ports 1 through 5 : (-mT) host:1-5Practical Use Case
scanning for mysql with http and https ports
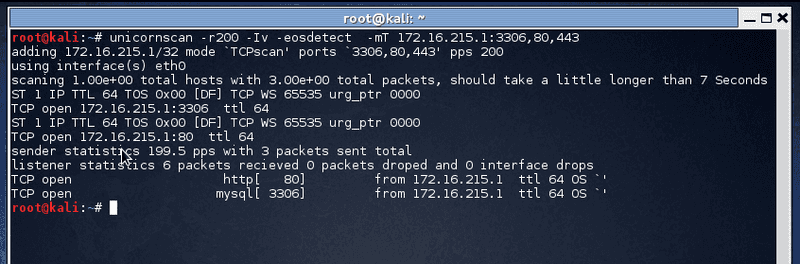
root@kali:~# unicornscan -r200 -Iv -eosdetect -mT 172.16.215.1:3306,80,443OUTPUT
TCP open 172.16.215.1:80 ttl 64
ST 1 IP TTL 64 TOS 0x00 [DF] TCP WS 65535 urg_ptr 0000
TCP open 172.16.215.1:3306 ttl 64
sender statistics 197.8 pps with 3 packets sent total
listener statistics 6 packets received 0 packets droped and 0 interface drops
TCP open http[ 80] from 172.16.215.1 ttl 64 OS `'
TCP open mysql[ 3306] from 172.16.215.1 ttl 64 OS `'HomePage : www.unicornscan.org
Getting Started : www.unicornscan.org/text/Unicornscan-Getting_Started.pdf