In this tutorial I am going to show you , how to install Fail2Ban in your ubuntu server and how to setup and configure fail2ban service to protect ssh against brute force attacks.
Install Fail2Ban
sudo apt-get update sudo apt-get upgrade sudo apt-get install fail2ban
It will install fail2ban for you just wait until it finish installing and setting things up .
now lets configure fail2ban
now change to /etc/fail2ban/ directory and make a copy of configuration file
cd /etc/fail2ban sudo cp jail.conf jail.local
by default jail.conf will load jail.local as configuration file , it means you can make changes in jail.local according your needs
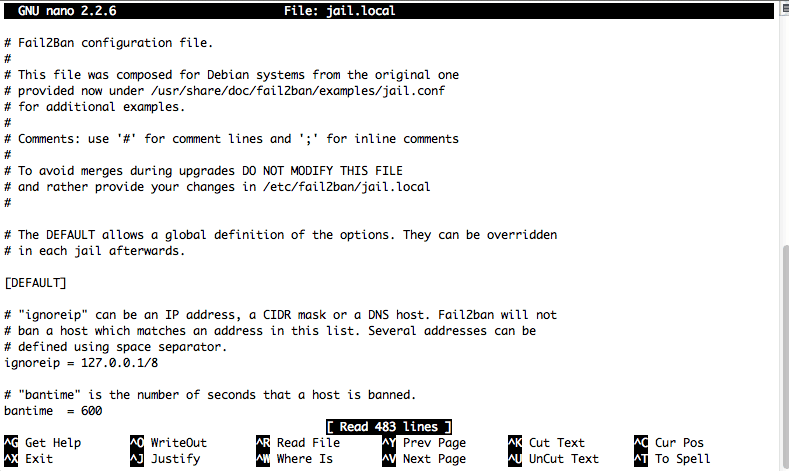
sudo nano jail.local
now edit some default setting , you can manually add some IP to ignored IP.
[DEFAULT] # "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not # ban a host which matches an address in this list. Several addresses can be # defined using space separator. ignoreip = 127.0.0.1/8 # "bantime" is the number of seconds that a host is banned. bantime = 600 # A host is banned if it has generated "maxretry" during the last "findtime" # seconds. findtime = 600 maxretry = 3
Change destination email to your email address
destemail = root@localhost
and finally change
action = %(action_)s
To
action = %(action_mw )s
If you want fail2ban for some other services just set # enabled = true in “SECTION_NAME”
If you want to configure some advanced filters and configure log filters take look at
/etc/fail2ban/filter.d
Now Restart Fail2Ban service and check IPTABLES Rules
sudo service fail2ban restart
See The Iptables Rules
sudo iptables -L
Some useful links :